5 minutes
Sign GitHub commits (using Mac)
Generally speaking, most organisations do not check if a commit is signed or not. Even worse, more companies do not care about this. It might subjective but I like to have the verified badge.
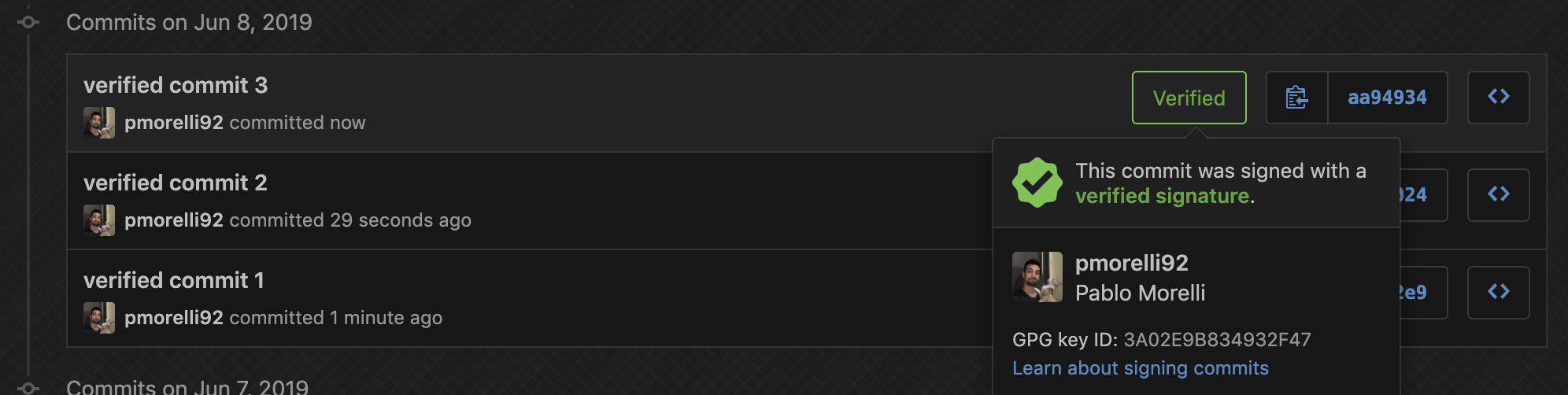
If you commit from GitHub, for example: adding or editing a README, you will get the verified bagde. The same will happen with the client GitKraken, but if you commit using the git cli this will not happen unless you configure it.
Now, I will assume that you are using a mac but in case you do not, you can google yourself some of the installation steps.
Installing GPG
In order to sign a commit you will need to generate a key, and for this you are going to use GPG . But first, you need brew to be installed, if you do not have it yet, it is a must have package manager for mac that you can download here .
> brew install gnupg
> brew install pinentry-mac
> echo "pinentry-program /usr/local/bin/pinentry-mac" >> ~/.gnupg/gpg-agent.conf
> killall gpg-agent
Pinentry as it is stated on the GPG site it is a collection of dialogs that allows you, for example, to input the passphrase of the private key. In order for this to work we need to indicate the path where it is installed into the GPG configuration and then kill the service (just in case) for it to take the changes.
Generating a set of keys
> gpg --full-generate-key
(you can customise the key creation or just press enter to use the defaults)
Will generate a private key from which you are going to generate and export the public key. The id of the key will be shown when you generate the key or you can fetch it by running:
> gpg --list-secret-keys
And you will get something like this:
sec rsa2048 2019-06-07 [SC]
KEY_ID_HERE
uid [ absolut ] Pablo Morelli <devandchill@gmail.com>
ssb rsa2048 2019-06-07 [E]
After you have your ID, execute:
> gpg --export --armor YOUR_KEY_ID 2> cat
You will see the public key on the terminal, now you can copy it and go to GitHub.
Adding public key to GitHub account
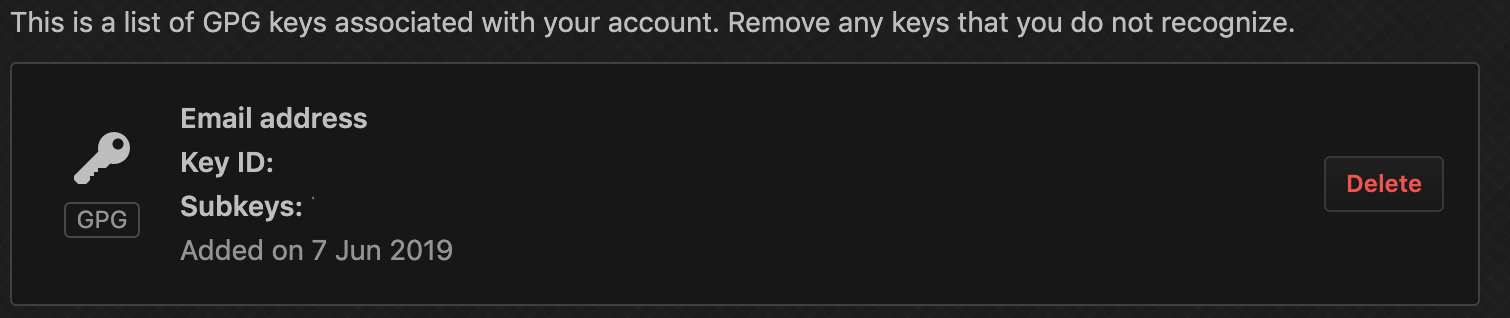
Go to Settings -> SSH and GPG Keys -> New GPG Key and paste the content of your key and after submiting you will see something like this.
Doing your first verified commit
When you work with the git cli there is a huge probability that you work with different accounts (for example one for work and one personal) and/or that you have more than one GPG key on your system.
To avoid problems with git not knowing which configuration to pick you will indicate that for the repo where you are standing or for all the repos you will use the GPG key that contains a certain ID.
> git config --local gpg.program "gpg"
> git config --local user.signingKey "YOUR_KEY_ID_INSIDE_THE_QUOTES" // will apply to the working directory
> git config --global gpg.program "gpg"
> git config --global user.signingKey "YOUR_KEY_ID_INSIDE_THE_QUOTES" // will apply to the all the repositories except when overriden
You are almost ready to go, but you need to know that by default git commit does not sign the commits unless you specify the argument -S. So you have two options:
> git commit -S -m "My commit message"
Or you can setup automatic signing for the repository or all the repositories.
> git config --local commit.gpgsign "true"
> git config --global commit.gpgsign "true" // if you want to set up for all the repositories
If you did the step above, the argument -S is no longer needed.
Checking git configuration
When you are unsure about your configuration you can execute git config --local -l to list the configuration for the working directory and you should see something like this:
gpg.program=gpg
commit.gpgsign=true
user.signingkey=YOUR_KEY_ID
Back up your private key
Keys are passwords, so you should save them somewhere safe and revoke + change periodically. It is trivial to revoke and to generate a new key for GitHub but it may be troublesome for some other systems that uses your public key. Now lets image that you change your computer, you wont be able to sign because you don’t have your key; in this case a backup is recommended.
gpg --export-secret-keys YOUR_KEY_ID > some_private_key_name
Now you can save this file to some secure vault, and if you ever need to import it on a new machine, execute:
gpg --import some_private_key_name
Bonus track
As I mentioned before, some times when you work using the git cli you end up mixing accounts, and it could happen to commit like this:
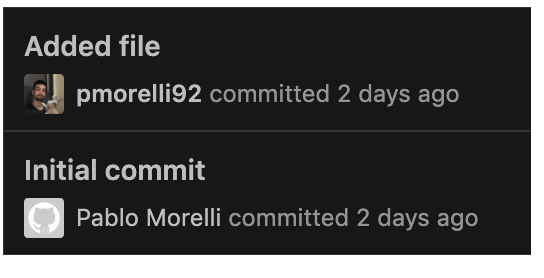
You can of course leave it like that or do a rebase of the commit; but you can also check first using git config --local -l which is the user.name and user.email for that working directory.
In case the email does not match with the email linked in GitHub you can change it doing:
> git config --local user.name "GitHub name"
> git config --local user.email "my.github@email.com"
I hope you liked the post, if so, don’t forget to share it so this can reach to more people :)